Hackers target Roundcube (update #3)

A previously unknown XSS exploit in Roundcube lets hackers inject JavaScript into the Roundcube server application. We are consulting on steps to take and options to repair the leak in Roundcube.
Update Oct. 27, 4:40 p.m.: All hosting environment have been patched. That’s nice going into the weekend!
Update Oct. 27, 2 p.m.: The patches for Roundcube are available and are currently being rolled out on all hosting environments. We expect the installation of the patch to be completed by 4 p.m.
Update Oct. 26, 3:37 p.m.: We are currently waiting on our vendor for a patch. As soon as the patch is available we will install it.
A team of hackers named Winter Vivern exploited a previously unknown vulnerability in the widely used webmail software Roundcube, researchers from the security firm ESET said on Wednesday.
This vulnerability (known as CVE-2023-5631) allows malicious actors, by sending a specially crafted email, to load arbitrary JavaScript code into the Roundcube user’s browser window. By viewing this email, malicious parties can ensure that emails can be sent from the affected Roundcube user’s mailbox.
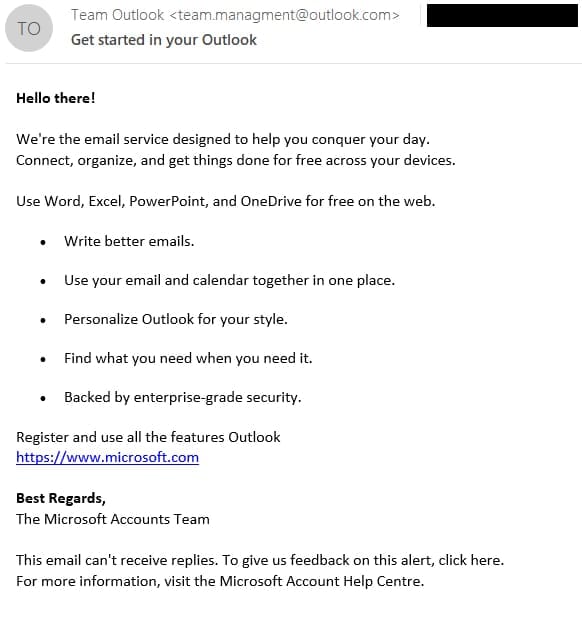
For more information on this leak in the Roundcube server application, we recommend this excellent Dutch-language article from ESET and this background article from ARS Technica.
We are currently in discussions both internally and with our suppliers about the steps to take and options for fixing the leak in Roundcube.
Workaround
It is possible to temporarily use an alternative application for webmail. This is a change made per domain name, not per user. To change the webmail application to SOGo follow this guide.